Computer Networks
A computer network can be described as a system of interconnected devices that can communicate using some common standard (called a protocol). These devices communicate to exchange resources (e.g. files) and services.
Here is an example network consisting of two computers connected together:
In the example above, the two computers are directly connected using a cable. This small network can be used to exchange data between just these two computers. It is fairly easy as each computer can only talk to the other. There are no other computers connected to talk to.
But what if we want to expand our network? Then we can use a network device, either a switch or a router, to connect more than two computers together:
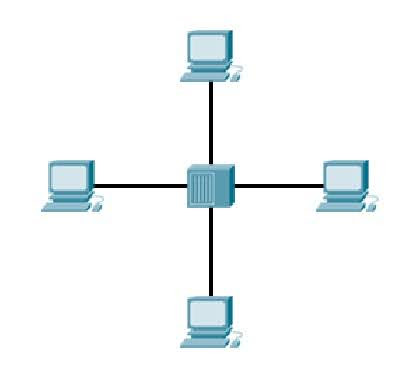
Now all of the devices on the network can communicate with each other. But how do they communicate with each other? How does the switch/router know who is talking to who?
OSI
The OSI (Open Systems Interconnection) model was created by the International Organization for Standardization (ISO), an international standard-setting body. It was designed to be a reference model for describing the functions of a communication system. It has seven layers, with each layer describing a different function of data traveling through a network.
From Bottom to Top:
- Application
- Presentation
- Session
- Transport
- Network
- Data Link
- Physical
Physical
Defines how to move bits from one device to another. It details how cables, connectors, and network interface cards are going to work and how to send and receive bits.
Data Link
Encapsulates a packet in a frame. A frame contains a header and a trailer that enable devices to communicate. A header, most commonly, contains a source and a destination Media Access Control (MAC) address. A trailer contains the Frame Check Sequence field, which is used to detect transmission errors.
The data link layer has two sublayers:
Logical Link Control – used for flow control and error detection.
Media Access Control – used for hardware addressing and controlling the access method
Network
Defines device addressing, routing, and path determination. Device (logical) addressing is used to identify a host on a network (EX: IP address).
Transport
Segments great chunks of data received from the upper layer protocols. Establishes and terminates connections between two computers. Used for flow control and data recovery.
Session
Defines how to establish and terminate a session between the two systems.
Presentation
Defines data formats. Compression and encryption are defined at this layer.
Application
This layer is the closest to the user. It enables network applications to communicate with other network applications.
The following table shows which protocols reside on which layer:
| Application | HTTP |
| Presentation | MiME |
| Session | SSL |
| Transport | TCP, UDP |
| Network | IP, ICMP |
| Data Link | PPP |
| Physical | Ethernet |
TCP/IP model
The TCP/IP model was created in the 1970s by the Defense Advanced Research Project Agency (DARPA). Like the OSI model, it describes general guidelines for designing and implementing computer protocols.
It consists of four layers: Network Access, Internet, Transport, and Application.
| TCP/IP Model | OSI Model |
|---|---|
| Application | Application; Presentation; Session |
| Transport | Transport |
| Internet | Network |
| Network Access | Data Link; Physical |
Encapsulation (Decapsulation)
The term “encapsulation” is used to describe a process of adding headers and trailers around some data.
For example, when you send an email message, that message is sent from the Application layer to the Transport layer. The Transport layer encapsulates the data and adds its own header (with its own information, such as which port will be used) and passes the data to the Internet layer, which again encapsulates the received data and adds its own header, usually with information about the source and destination IP addresses. The Internet layer then passes the data to the Network Access layer. This layer is the only layer that adds both a header and a trailer. The data is then sent through a physical network link.
Each layer adds its own information:
| Frame Header | IP Header | TCP Header | Data (Content) | Frame Trailer |
The term “decapsulation” refers to the process of removing headers and trailers as data passes from lower to upper layers. This process happens on a computer that is receiving data.
Frame, Packet, Segment
Frame – the term “frame” refers to the encapsulated data defined by the Network Access layer. A frame can have a header and a trailer that encapsulate a data section.
Packet – the term “packet” is used to describe the encapsulated data defined by the Internet layer. A packet can have a header with the source and destination IP addresses.
Segment – the term “segment” describes encapsulated data defined by the Transport layer. A segment can have a header with information such as source and destination port numbers, sequence and acknowledgment numbers, etc.
Ethernet
Ethernet is the most used networking technology for Local Area Networks (LANs) today. It defines wiring and signaling for the Physical layer of the OSI model. For the Data Link layer, it defines frame formats and protocols.
Ethernet is described in the IEEE 802.3 standard. It uses the Carrier Sense Multiple Access with Collision Detection (CSMA/CD) access method and supports speeds up to 100 Gbps (currently). It can use coaxial, twisted pair, and fiber optic cables. Ethernet uses frames with both a source and a destination MAC addresses to deliver data.
Remember encapsulated data defined by the Network Access layer is called a frame. An Ethernet frame starts with a header, which contains the source and destination MAC addresses, among other metadata. The middle portion of the frame contains the actual data. The frame ends with a field called a Frame Check Sequence (FCS). The FCS allows for frame contents to be checked against for any corruption.
The Ethernet frame structure is defined in the IEEE 802.3 standard for Ethernet.
| Preamble | SFD | Dest. MAC | Source MAC | Type | Data and Pad | FCS |
| 7 bytes | 1 byte | 6 bytes | 6 bytes | 2 bytes | 46-1500 bytes | 4 bytes |
Preamble – informs the receiving system that a frame is starting and enables synchronisation.
SFD (Start Frame Delimiter) – signifies that the Destination MAC Address field begins with the next byte.
Destination MAC – identifies the receiving system.
Source MAC – identifies the sending system.
Type – defines the type of protocol inside the frame, for example IPv4 or IPv6.
Data and Pad – contains the payload data. Padding data is added to meet the minimum length requirement for this field (46 bytes).
FCS (Frame Check Sequence) – contains a 32-bit Cyclic Redundancy Check (CRC) which allows detection of corrupted data.
MAC Address
A Media Access Control (MAC) address is a 48-bit address that is used for communication between two hosts in an Ethernet environment. It is a hardware address, which means that it is stored in the firmware of the network interface card (NIC).
A MAC address is intended to be globally unique. Each network card vendor gets its share of addresses (represented by the first 24 bits).
The address is written in the form of 12 hexadecimal digits. For example, consider the following MAC address:
D8-D3-85-EB-12-E3
Every hexadecimal character represents 4 bits, so the first six hexadecimal characters represent the vendor (in this case a Hewlett Packard card, like in our Appian laptops).
How to find out your own MAC address?
If you are using Windows, enter the Command Prompt (Start – Programs – Accessories – Command Prompt).
Type ipconfig/all and you should see a field called Physical address under the Ethernet adapter settings listed.
If you are using Linux, type the $ ifconfig command. You should see your MAC address referred to as HWaddress.
IP Address
An IP address is a 32-bit number that identifies a host on a network. It is usually written in the form of four decimal numbers separated by periods (EX: 10.0.50.1).
In contrast to a MAC address, an IP address is a logical address. Any device that wants to communicate with other devices using TCP/IP needs to have an IP address. It can be configured manually or it can be obtained from a DHCP server.
The term “IP address” is usually used for IPv4, which is the fourth version of the IP protocol. A newer version exists, IPv6, which uses 128-bit addressing.
Private IP Addresses
There are three ranges of addresses that can be used in a private network. These addresses are not routable through the Internet.
Private addresses ranges:
- 10.0.0.0 – 10.255.255.255 (10.0.0.0/8)
- 172.16.0.0 – 172.31.255.255 (172.16.0.0/12)
- 192.168.0.0 – 192.168.255.255 (192.168.0.0/16)
How to find out your IP address
For Windows, enter the Command Prompt (Start – Programs – Accessories – Command Prompt). Type ipconfig and you should see a field called IP address.
For Linux, enter ifconfig in the terminal and you should see a field called inet addr.
CIDR Notation
A CIDR (Classless Inter-Domain Routing) notation is a compact representation of an IP address range. It is constructed from an IP address, a slash character and a decimal number ranging from 0 to 32.
Examples: 172.30.0.1/32, 10.0.0.0/8, 52.4.5.0/24.
To calculate the range of a CIDR block (say 10.0.0.0/N where N is a decimal number between 0 and 32), use the following formula: 232-N .
Examples:
- If N=32, 232-N = 1 and 10.1.1.1/32= 10.1.1.1
- If N=31, 232-N = 2 and 10.1.1.1/31= {10.1.1.1, 10.1.1.2}
- If N=30, 232-N = 4 and 10.1.1.1/30= {10.1.1.1, 10.1.1.2, 10.1.1.3, 10.1.1.4}
- If N=24, 232-N = 256 and 10.1.1.0/24= 10.1.1.0 – 10.1.1.255
- If N=16, 232-N = 65536 and 10.1.0.0/16= 10.1.0.0 – 10.1.255.255
- If N=8 and 10.0.0.0/8= 10.0.0.0 – 10.255.255.255
- If N=0 and 0.0.0.0/0= 0.0.0.0 – 255.255.255.255 (All IP addresses)
You should be able to easily determine the range if N=32,24,16,8 and 0. For other ranges, feel free to use an online CIDR block calculator to get the range.